The Paxton Net2 Software is an advanced access control software solution designed to work in tandem with the Paxton access control product range. Basically, the Paxton Net2 Software is designed to manage all physical access control systems under one centralised system. For example, allocating their proximity key fobs to allow access to their physical turnstile barriers.

We can now simplify the management of building access control. Additionally, this can be monitored and managed through one or more PC systems. We can now provide your business with a complete solution for wireless door entry. “Developed to be straightforward and intuitive, the Net2 software is very easy to learn.”
Who Are Paxton?
Paxton is a global company with access to exports in over sixty countries worldwide. Paxton’s UK-based headquarters is situated in the seaside town of Brighton. They have accumulated over thirty years of experience in designing and manufacturing access control and security systems.
As a British manufacturer with decades of experience, Paxton offers unrivalled technical support to their market-leading products. Their products are easy to install across a multitude of industries including education, healthcare, leisure, retail, commercial and the public sector.
In addition, Paxton has worked with huge brands such as Graze, Manchester United, Michelin, Sky and Foyles. We are certain that you will enjoy working with this brand as much as we do.
What Is Access Control?
Access control is the process of controlling access to a building, area or object. It can include both physical and electronic security measures with additional software management systems if necessary. Access control systems can be utilised in a variety of applications such as commercial buildings where stricter office access is needed. These buildings can include banks, retail stores and offices.
One thing that many people do not realise about access control is that it’s not just about the doors. Access control can be used to control access to physical spaces, laptops, tablets and phones as well. How does an Access Control System Work? An access control system is used to track who has access to the spaces of your building, such as offices and workstations. It can also be used to track which areas are occupied at any given time, which may be useful for security purposes.

The Importance of Access Control
Security access control is a crucial part of any business. It’s a way to protect your employees, customers and assets from harm. In addition, we can ensure that the right people are in the right places at the right times.
Manage Access
Access control is a system that allows you to control who has access to your entire building. What’s more, it can be used to manage who has access to what parts of your facility or building. Also, this is so that only those working on specific projects or tasks have access when they need it.
Also, this reduces the risk of exposing your company’s client base. If clients trust that you can protect their confidential documents, you can maintain healthier working relationships.
The system can be used to track who enters and leaves the building, or it can be set up so that people only have access during certain times of the day. This is a great way to ensure that only authorised personnel are able to enter your building at any given time.
Tracking Movement
Beyond keeping people out, access control systems can track who is on-site and at what time. This helps you keep tabs on productivity, as well as accountability.
For example, if you were to install an access control system at your office or factory and then set it up so that anyone who wants to go into that building must swipe their card through a reader to gain entry, you’ll be able to see how many people are coming in at what times of day.
You can also use this technology for tracking employee movements throughout the workday. Did someone go where he was supposed to go? Did they spend too long somewhere else? Were there any deviations from normal behaviour?
You’ll have answers to all these questions once you’ve installed an access control system in your workplace and set up rules about which doors require swiping cards.
Types of Security Access Control
Security access control, also known as security systems, is a system that is used to monitor and restrict access to a building, room, or other areas. The term “control” refers to the act of controlling who has permission to enter or exit an area. There are three types of security access control systems: physical, logical, and biometric.
Physical Security Systems
Physical security systems use physical barriers like keys or turnstiles to limit access in some way. They can be used on their own or in conjunction with another type of system.
Logical Layers
Logical layers include software-based authentication methods such as usernames and passwords. These do not require any special hardware at all but instead rely on existing computers for execution.
Biometric Layers
Biometric means “measuring biological traits,” so this refers specifically to a system that uses certain aspects of your body (such as fingerprints) as its method for determining whether you should be granted entry into a specific location. This could mean both physical locations like buildings but also digital ones like websites.

Paxton Net2 Software, The Benefits
Intuitive, easy to learn and free of charge, these are some of the reasons you need to download the Paxton Net2 software. Compared to other systems, this is an advanced PC-based access control solution. Above all, Paxton Net2 works as a centralised solution. Especially popular, this solution works for up to 1,000 doors and 50,000 users.
What Is Checkpoint Control?
Checkpoint control is a form of access control that restricts entry into restricted areas. As with all access control systems, checkpoint control requires some type of identification to make sure people have permission to pass through checkpoints (doors).
Checkpoint control is a way to control who enters and leaves your premises. It can be used in many different types of facilities, including airports, manufacturing plants and office buildings.
Checkpoint control can be used to prevent unauthorised access to restricted areas. It also can help protect your people from theft by ensuring that only authorised personnel are allowed into a particular area.
Checkpoint Control – Paxton Net2 Software
- Approve and monitor building access.
- Monitor staff and visitor locations.
- Validate people before granting access.
- Implement stricter health and safety protocols.
Paxton Net2 Checkpoint Control – Paxton encourages premises to utilise this software when monitoring and approving building access. Further to this, it can be beneficial when monitoring employees, visitors and those attempting unauthorised access.
Creating checkpoints is the process of requesting access validation from entrants. We can create manned access points within a building where entrants need to be validated before access. This allows for building segmentation e.g. everyone will have access to reception areas, however, managers will have access to office space upstairs.
We can use Paxton Net2 Software to follow stricter health and safety or emergency evacuation protocols.
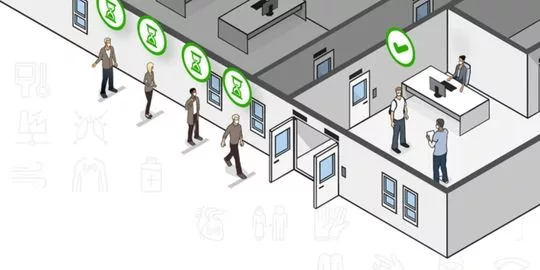
What Is Occupancy Management?
Occupancy management is the control of people in and out of your building. It’s used to reduce congestion and maximise social distancing in public spaces like hospitals, and retail.
It’s about managing who goes where, when and for how long. The system not only monitors who enters or exits a building but also allows you to see who’s in each room or space at any given time.
The goal of occupancy management is to minimise congestion and maximise social distancing.
Occupancy Management – Paxton Net2 Software
With Paxton Net2 Software, you are guaranteed updates that add incredible features to your system. One of the latest features includes occupancy management. This is the process of managing the flow of people around your building. Additionally, this software now allows businesses to maximise the number of people in any given area whilst maintaining social distancing measures.
many businesses are focusing on improving their social distancing policies with Winter coming soon and the potential of the virus spreading.
What Is A Security Lockdown
A security lockdown is a highly restrictive, temporary procedure for dealing with critical situations. Lockdowns may be used as a means of protecting people from harm.
A lockdown is a procedure to keep people safe and secure during emergency situations that involve violence or the possibility of violence, or as a precaution against security breaches.
Security Lockdown – Paxton Net2 Software
- Close off areas of your building from the public.
- Maintain free movement for security personnel.
- Display the last known locations of users.
- ‘Who’s in’ feature to identify people still within the building.
- Keep confidential information private.
Paxton Net2 software security lockdown is perfect for premises with confidential information storage. Most important, in the event of an emergency, you are able to close off areas of the building from the public. However, security personnel will still have free movement.
Similarly, with the ‘who is in?’ feature you can clear a building effectively. However, this feature will display the last known location of a user based on where they last presented their access fob/card.
What Is A Digital Clocking-In System?
A digital clocking-in system is a system where employees clock in and out of their shifts using digital methods rather than paper methods. This can be done through a special access reader that scans employee ID badges or fingerprints. Having an online time clock system can help businesses save money by automatically calculating employee time and by reducing time theft or human errors in payroll calculation.
Digital Clocking-In System – Paxton Net2 Software
Use a proximity reader from Paxton to analyse and report on employees’ time spent in the business on any given day. Once this system is installed we are able to export reports and send these directly to human resources for payroll processing.
What Is ID Image Verification?
User image verification is the process of confirming a user’s identity by comparing a self-uploaded photo of their face and their government-issued photo ID. This helps companies to be certain that the user submitting an ID or selfie submitted is also the person holding that ID.
Image Verification – Paxton Net2 Software
The Paxton Net2 Software allows security to match an entrant or employee’s government ID with their uploaded image to confirm they are not using fake IDs to access unauthorised areas.
Core Software Benefits – Paxton Net2 Software
- Install it onto as many PCs as you wish.
- Add up to 50,000 users into the system.
- Grant and remove access as required.
- Implement temporary access permissions which expire.
- Customise login and home screen pages with your branding.
With Paxton Net2 software you are able to freely install this onto as many PCs as physically necessary. Since there is no restriction, up to 50,000 users can be added to the system if required.
Paxton Net2 software is intelligent enough to allow administrators to grant or remove access to other users if needed.
Suprisingly, temporary access permissions mean that administrators can allow access permissions for a set period of time. This can be both temporary upgrading or downgrading of permissions.
To demonstrate the flexibility of this system, image verification can be used via the Paxton Net2 software. You can visually confirm the user’s identity.
Lastly, once logged into the system the welcome page can be customised. You can display your company’s logo, contact details and support contact number.
Conclusion
Security access control is a great way to ensure your building’s security. Also, it can also provide you with peace of mind. If you have a large commercial property or multiple locations, this system can help you keep track of who has access at all times. It’s important to remember that the safety of your employees, customers and visitors depends on how well you manage security access control systems. If you’re looking for a company that provides secure access control systems, give us a call today. We can help you find the solution that best meets your needs and budget.
Additionally, if you have any questions about security access control, please contact us today. We’re always happy to help with your security access control needs.