An access control system is crucial. The combination of internet technology, encryption and security will form the basis for a strong access control system. Firstly, a vast number of businesses and institutions can benefit from the installation of these security systems. These systems allow companies to retain confidential information by implementing preventative measures for unwanted access.
Originally, an access control system consisted of a door, a lock and a key. Over time we continue to push technological progress, and smarter technology is now far more accessible.
Commercial premises with heavy footfall will have many reasons for the installation of a high-quality access control system. However, basic forms of access control can be implemented into domestic premises.
Access control systems are available in a wide range of options. They can be configured to suit your needs and budget, so it’s important to consider what you want from your system before deciding on what type of access control is right for you.
What Is Access Control?
An access control system, simply, allows the user to control access to and from their premises. We would often refer to access control as intelligent technology capable of managing access to private resources in a secure environment.
In a commercial setting, businesses are now able to manage and monitor the granted access for both members of the public and employees. Additionally, employee hours and movements can be tracked via these systems which aid human resource and finance departments when calculating payroll data.
Access control systems are used to restrict access to areas within a building or campus. Once authorised they will be granted entry into a location or system. Generally, access control will use technology to authenticate users by identifying who they are. The technology used may include cards, access fobs, fingerprint scanners etc.
The system is then programmed with a list of access holders, for example, managers with access fobs. Once profiles have been created, we can allocate permissions based on their necessary building access. An example may be that visitors can only access reception areas, employees have office access and managers have human resources access.
An access control reader would then be installed on the outside of the access door (or gate). The reader can be programmed to recognise the fob or card and grant access. If a person is not authorised, they will be denied entry.
Access control systems are not only used for security. They can also be implemented as a means to monitor who enters and exits certain areas of a building. This is important in preventing loss of stock, theft and ensuring compliance with health & safety regulations.

Features Of Access Control
In this modern era, advanced access control systems aid in the tracking of individuals entering and leaving the property. In addition, we use access control as a security measure against theft or vandalism. There were 266,283 burglaries in England and Wales during 2021/22 and so access control would be useful in combatting this criminal activity within your premises.
The access control system is made up of various components that work together to monitor the activities of individuals. Our systems consist of hardware, software and networking components. They may also include biometric scanners or magnetic cards to further enhance security measures. Our access control systems are designed to meet the needs of a variety of commercial, industrial and residential applications. We offer a wide range of products and services that can be customised to suit your requirements. With our expertise in this field, we are able to provide you with the right solution for your needs.
Features: Tracking Personnel, Guests and Intruders
An access control system can provide real-time reports on who is on-site and at what time. This helps you keep tabs on productivity, as well as accountability.
For example, imagine you set up an access control system at your office or factory and then programmed it so that everyone who wanted to go inside had to swipe their card through a reader. You would be able to see how many people entered the building and when they did so.
This technology can also be used to track employee movements throughout the workday. Did someone go where he was supposed to go? How long did she/he spend somewhere else? Was there any deviation from normal behaviour? Once you’ve installed an access control system in your workplace and set up rules about which doors require swiping cards, then you’ll have answers to all these questions.
Features: Check Point Control
Checkpoint control is a form of access control that restricts entry into restricted areas. Like all forms of access control, checkpoint controls require some type of identification, such as an ID badge or fingerprint scan to ensure people have permission to pass through the door.
Checkpoint control is a means of controlling the flow of people in and out of areas such as airports or manufacturing facilities. Checkpoint control can be used to restrict access to certain areas and also safeguard personnel from theft by ensuring that only authorised people are allowed into a particular area.
This is a means of controlling the flow of people in and out of areas such as airports or manufacturing facilities.

Features: Security Lockdown
A lockdown is a highly restrictive procedure for dealing with critical situations. It may be used as a means of protecting people from harm. Lockdowns are emergency procedures undertaken by authorities to ensure the safety of people in a given area.
A lockdown is a highly restrictive procedure for dealing with critical situations. It may be used as a means of protecting people from harm or to ensure that only authorised people are allowed into a particular area.
Features: Occupancy Management
Occupancy management is a way of controlling the number and flow of people through spaces like hospitals, retail stores and airports. It’s about controlling who goes where, when and for how long. The system allows you to see who is in each room or space at any given time and even see video live feeds if necessary.
One goal of occupancy management is to ensure that people who are in close proximity stay as physically distant from each other as possible. The system can automatically lock doors and restrict access to areas, depending on the situation. If a patient or visitor needs to be moved from one room to another, this can be done by simply entering their information into the system.
Sectors In Need of Access Control
As you’re aware an access control system is used in many sectors and industries. From a corporate perspective, access control systems are used to maintain security and prevent unauthorised entry. This is particularly important for businesses that have high-value items or information to protect. Examples of these include data centres, server rooms and businesses with expensive stock such as jewellery or clothing.
As well as high-value items, access control is often found in office buildings and many smaller areas including train station toilets, football stadiums or airport security. Additionally, retail, healthcare, hospitality, education campuses, festivals and high-security environments all have some form of access control.
The systems are used in a variety of locations such as:
- Domestic Homes.
- Care Homes.
- Apartment Buildings.
- Secure Entryways.
- Vehicles.
- Locking Doors.
- Business Premises.
- Festivals.
- Toilets.
Other points of entry into the premises by using an access card reader that logs each individual who passes through the doorway.

Types of Access Control
Access control systems ensure that only authorised individuals have access to a given location. It enhances the security of the property by limiting who gets in and out. Security systems also detect when people enter or exit areas, allowing you to monitor their movements.
There are many different types of access control systems, but they all serve the same purpose. They allow you to securely control who is allowed into a building or onto a property. You can use them for homes, businesses and anywhere else that needs security.
Physical Layer Security Systems
Physical security systems use barriers like keys or turnstiles to limit access. They can be used on their own or in conjunction with another type of system. There are many different types of physical security systems, but they all serve the same purpose. They allow you to securely control who is allowed into a building or onto a property. You can use them for homes, businesses and anywhere else that needs security.
Logical Layers
Software-based authentication methods, such as usernames and passwords rely on existing computers for execution. They are considered the logical layers of security. They are used to control access to computer systems and data, and rely on the physical layer for execution. The combination of logical and physical layers is what makes a complete security system.
Biometric Layers
Biometric refers to a technology that uses physical features (such as fingerprints) to determine whether someone is allowed into a specific location. Biometrics are considered the biological layers of security. They use human characteristics, such as fingerprints and retina scans, to verify a person’s identity. They can also be used for authentication purposes in everyday life (for example, when unlocking your smartphone). Biometric security systems are very accurate, but they are also relatively expensive. They can be used in conjunction with other security systems to make them more secure and efficient.
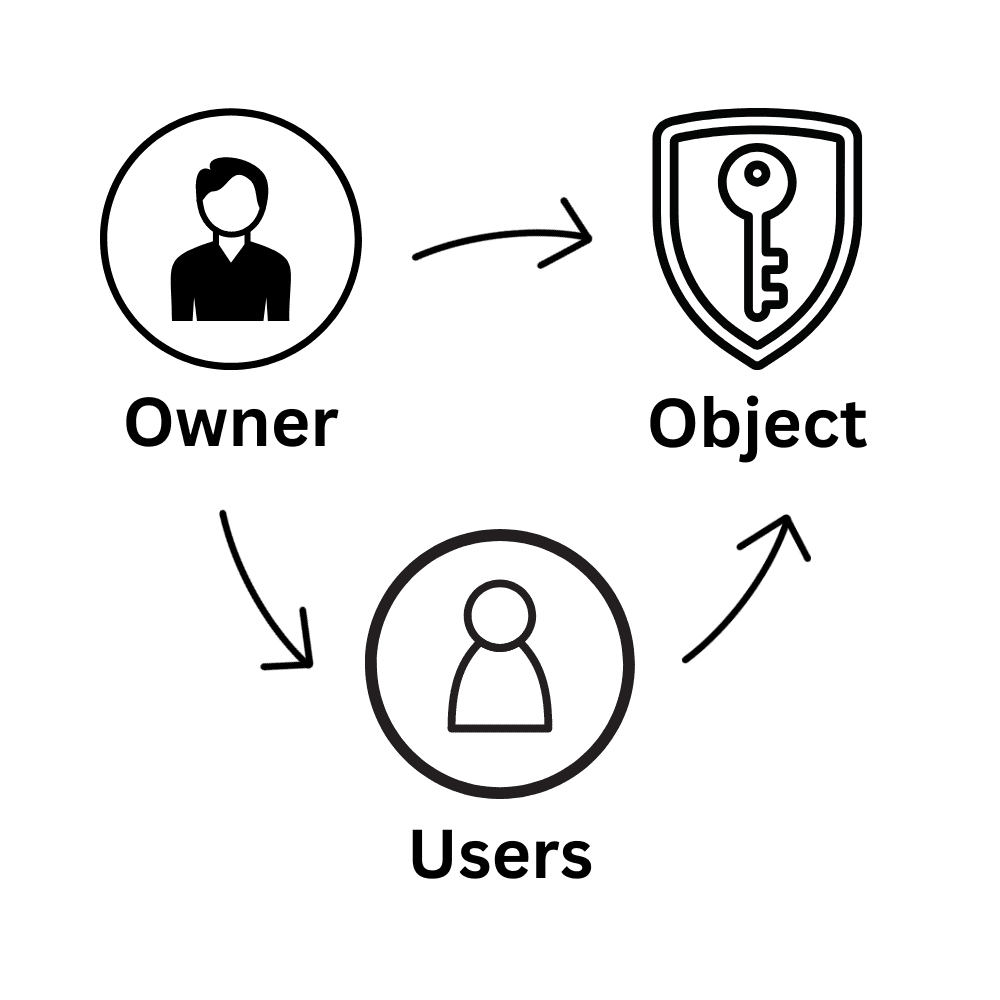
Discretionary Access Control
Discretionary access control is identity-based. These measures of access control provide users with control of their data and therefore are the perfect choice for homes and smaller businesses. Discretionary security access control will allow the resource owner to provide access to whomever they wish. The owner can also restrict object access via user identification, username and password.
The Basic Principles of Discretionary Access Control
- Object characteristics (size, name, directory path) are invisible to users that aren’t authorised.
- Several failed access attempts enforce additional multi-factor authentication or deny access.
- Users can transfer their object ownership to other users. Also, the owner determines the access type of other users. Based on these access privileges, the operating system decides whether to grant access to a file. (source)
Discretionary access control has many pros including that it’s extremely user-friendly. This means that users can quickly access data. These access control systems are flexible and easy to maintain. The only con to this form of access control is that data protection isn’t as reliable.
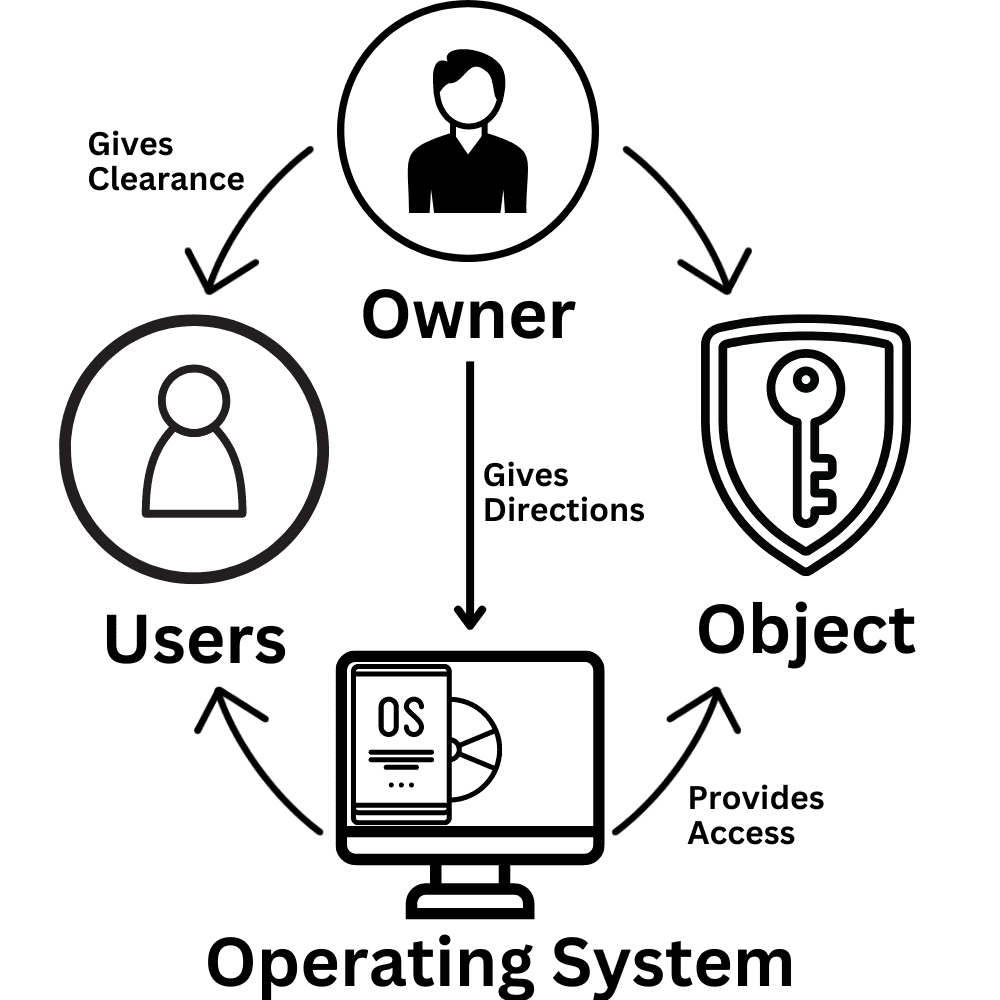
Mandatory Access Control
Compared with a discretionary access control system, a mandatory access control system has a higher level of security. Mandatory access also ensures that the end user doesn’t control who has access to the premises. With a mandatory access control system, only the system administrator and owner can manage access control.
Although this is a viable option for securing any type of property, it’s best suited to small and medium-sized businesses. Adding and removing access to relevant areas is a time-consuming process that involves no automation. This wouldn’t be practical for businesses with a large number of employees.
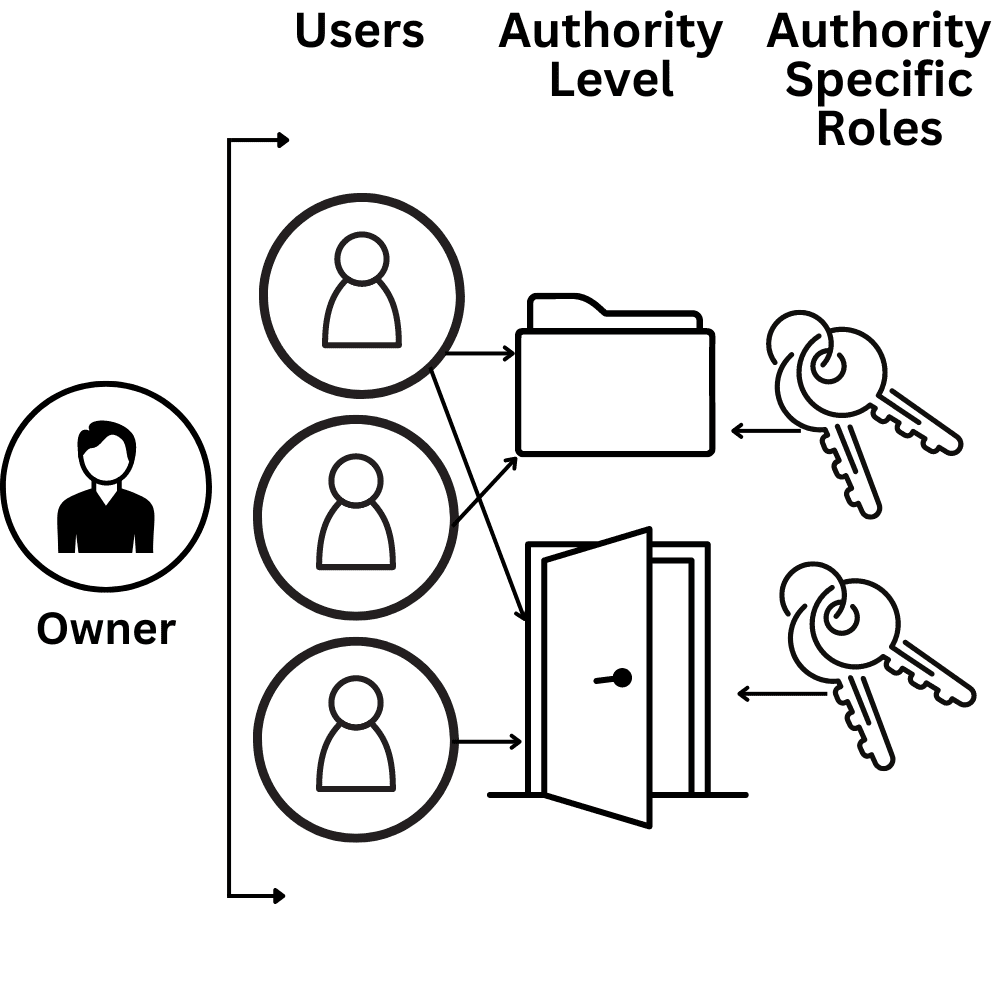
Role-Based Access Control
Role-based access control (RBAC), is an access control system that restricts network access based on a person’s role within an organisation. This has become one of the main methods for advanced access control in a business. The roles in RBAC refer to the levels of access that employees have and this is based on their function within the company itself. Using RBAC can restrict access to computer resources such as programs and modifying files.
Conclusion
Access control systems can be used to restrict access to areas within a building or campus. It is often used in conjunction with other security measures such as surveillance cameras, alarms and guards. The system is programmed with a list of cardholders and their permissions. In addition, permissions can be granted and revoked at any time depending on what’s needed.
There are many benefits to having an access control system. It makes it much easier to keep track of who has entered and left a building, as well as whether they have the right permissions. It also ensures that only those with access can enter certain areas; this is particularly useful in high-security environments such as banks.